Mobile carriers with Managed Security Service Providers have the opportunity to address and solve some of the challenging cybersecurity issues threatening consumers and businesses alike, such as hardware-level vulnerabilities, encryption hacks, and inter-application data breaches, that are increasing the risk to privacy protection in the world of GDPR.
The Era of Privacy First – A New Frontier of Consequence
Having your customer’s personal data compromised has just gotten much riskier and dangerous for your business. With the advent of GDPR (General Data Protection Regulation), which has gone into effect on May 25th of 2018 across the European Union, businesses are now coming to grips with the imminent reality that an empowered consumer and the protection of their privacy has become a critical business reckoning and imperative, not just a technology concern. Failure to uphold the requirements of GDPR has significant monetary consequences for businesses that do not properly administer and protect personal data.
Figure 1: Privacy Risk Vectors
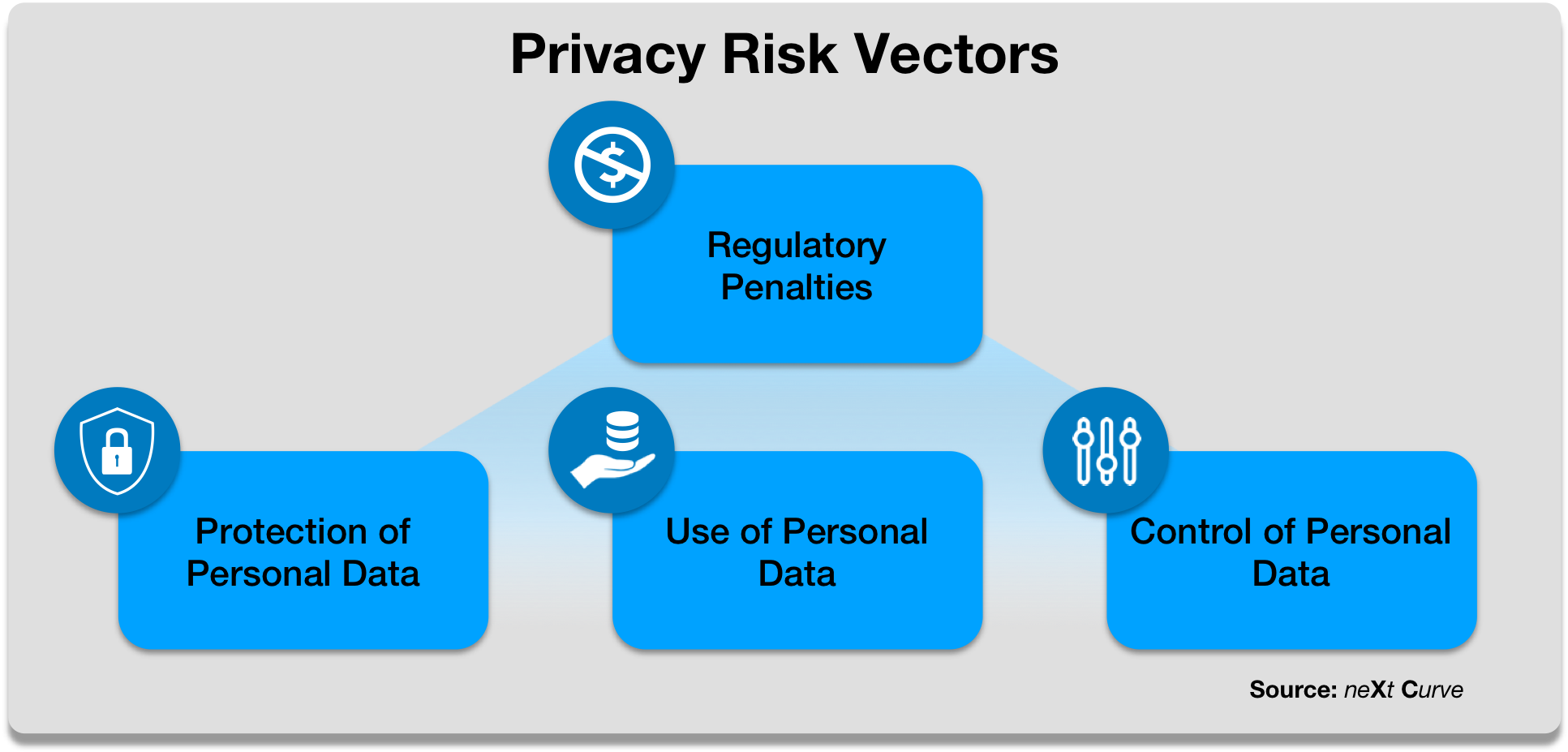
The consequences of GDPR violations and non-compliance are emblematic of a fast-emerging trend toward giving consumers control and enhanced custodianship of their personal data and privacy.
- GDPR regulatory penalties can be up to €20m or up to 4% of global turnover for an enterprise, whichever is greater.
- Increasing government and consumer concerns about privacy and privacy protection have market and non-financial implications for a business. For example, Facebook’s $100 billion drop in valuation during the Congressional hearing on their providing private information of an estimated 87 million users to Cambridge Analytica, and Cambridge Analytica’s subsequent insolvency and closure on March 28, 2018.
In addition to higher stakes for regulatory violations and non-compliance, GDPR has significant technological and organizational requirements for businesses to protect and administer the use of personal data. The key requirements fall into three categories that must be owned and managed by a new, mandated role, the Data Protection Officer:
- Protection of Personal Data: Take a risk-based approach to data protection and security, by assessing, monitoring and plugging all vulnerabilities, and notifying authorities when personal data has been compromised.
- Use of Personal Data: Disclosure and consent in the use of personal data with a lawful basis for processing such personal data.
- Control of Personal Data: Provide individuals with control of the provisioning and permitted use of their personal data including the right to erasure, data portability, and visibility to their personal data held by a processor or data controller.
While security (network security, IoT security, application-security) is a critical piece in privacy, privacy regulations like GDPR have additional elements like policy enforcement, monitoring, control and reporting, to flag and control a rogue IT administrator as an example, or someone internally casually looking at a customer’s private data. So, a business can be secure, but still be non-GDPR compliant. And an insecure firm, is most definitely non-GDPR compliant.
The Expanding Universe of Cybersecurity Threats
As the bar of privacy protection is set higher, new forms of cyberattacks are occurring daily across an expanding landscape of vulnerabilities, exposing businesses and individuals in a GDPR world to significant risk. According to NTT Security’s recent report: “2017 Global Threat Intelligence Report”, there was a notable increase in the number of security events during Q3 ’17, up 24 percent from Q2 ‘17. To make matters more concerning, 30 percent of insider threats will put an organization at risk without the organization even knowing it.
We see four security threat vectors putting individuals and businesses at increasing privacy risk going forward.
Figure 2: Key Security Threat Vectors
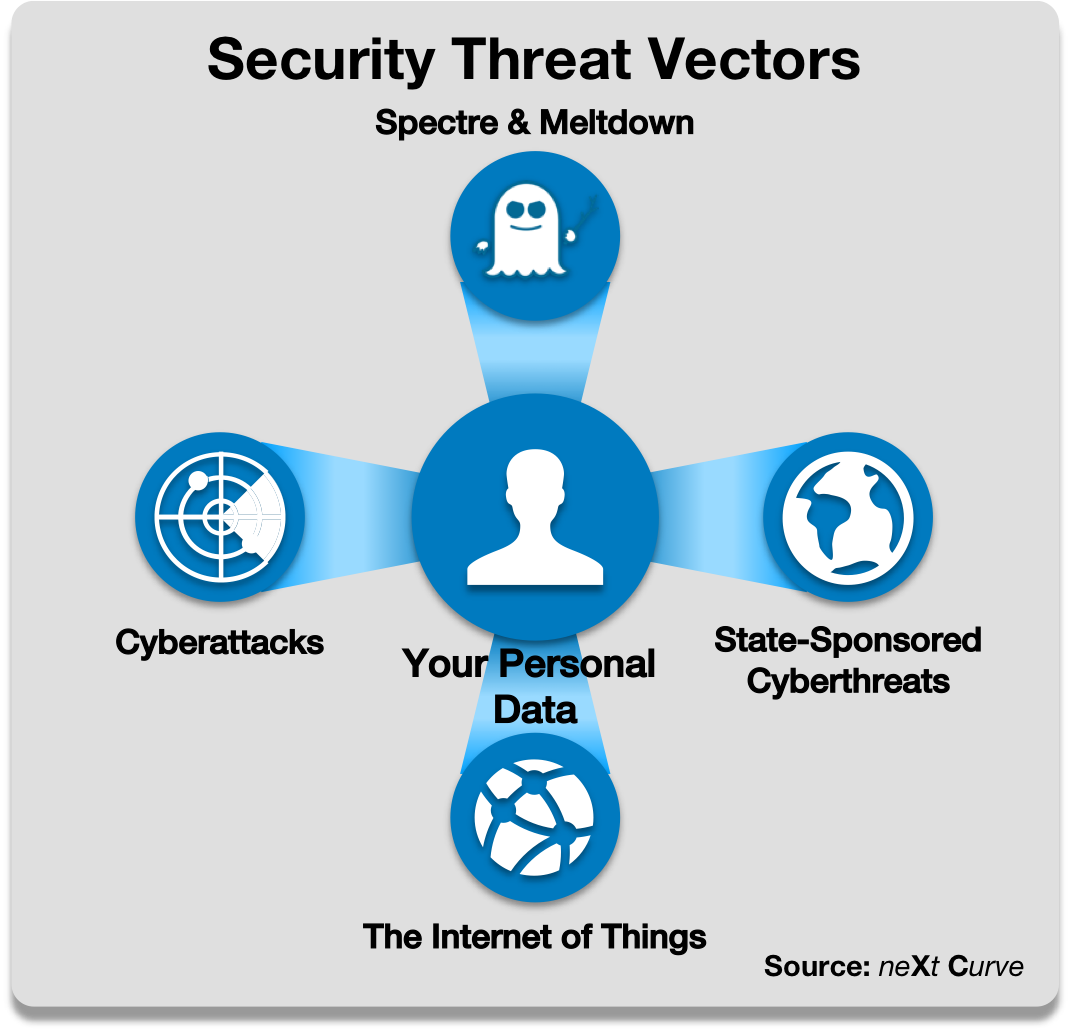
As IoT continues to expand its footprint into the lives of consumers, individuals and businesses are exposed to a fast-growing threat landscape that makes personal data increasingly vulnerable to attack due to the generally insecure state of IoT implementations today. Recent IoT security breaches exemplify privacy as well as significant safety concerns such as the Jeep hacking in 2015, mobile robot hackings like the Softbank Pepper hacking in early 2017, to the Devil’s Ivy vulnerability found in many video surveillance gear discovered in the summer of 2017. In mid-Oct. 2017, RSA keys generated by Infineon chips used in Smartcards, and IoT devices were found to be vulnerable to hackers.
There are also increasing concerns about state-sponsored cyberattacks aimed at high-value targets and their potential to disrupt key infrastructure and assets that could result in public safety compromises and economic harm. In September of 2017, Kaspersky’s malware detection software was reported to have been exploited by Russian and North Korean hackers to acquire classified data from U.S. and South Korean government systems.
In January of 2018, Spectre and Meltdown vulnerabilities were exposed in many of Intel’s and AMD’s CPUs and some ARM chipsets among others. Though firmware patches have been issued it will be a year or more before new processors with remediated designs are shipped. Spectre and Meltdown present a security risk at the processor level that impacts many categories of processors produced since 1995 raising security concerns across a broad range of devices including servers, network equipment, smartphones, PCs, smart speakers and more that are in service today.
GDPR compliance would fail from security breaches where passwords can be obtained, and personal data could be accessed and perhaps modified. Yet, businesses are challenged to prepare themselves to comply with new GDPR requirements. According to Gartner, by the end of 2018, less than 50% of businesses will be ready for GDPR, with the required enhanced security monitoring, control, and reporting. According to TechRepublic, 60% of firms are likely to miss the GDPR deadline.
While established technology firms like Google, Microsoft, Facebook, and IT/Telecom firms should have the resources to achieve GDPR compliance for their own applications and be able to address the security vulnerabilities as they arise, it’s the small and medium-sized businesses with limited IT resources and budget that are most vulnerable to non-compliance and the penalties that come with it. Already firms like the LA Times have shut down their European websites, due to non-compliance with GDPR, which already is impacting their revenues. And on May 24, Twitter announced that the company will no longer support video-based apps for Roku, Android TV devices or Microsoft’s Xbox for partner applications, which may be GDPR compliant individually, but are not compliant as a bundled offering through Twitter’s social platform where shared user data exists.
Finding and Integrating Needles in The Haystack
As businesses struggle to put the appropriate security and privacy protections in place to meet the GDPR regulatory requirements, their challenge is continual in dealing with a broad fragmented landscape of cybersecurity vendors to address increasingly complex security threats and scenarios. Historically, security solutions were from fixed appliance vendors with firewalls, software vendors with malware detection and removal, and hosted offerings from managed security service providers, data center hosting providers, and fixed operators offering VPN connections. Can a new, holistic, integrated security and privacy platform be offered as a service by the mobile operator with holistic management, monitoring and control, through an ecosystem of trusted partners?
Figure 3: Vendor Landscape of Cybersecurity Solutions
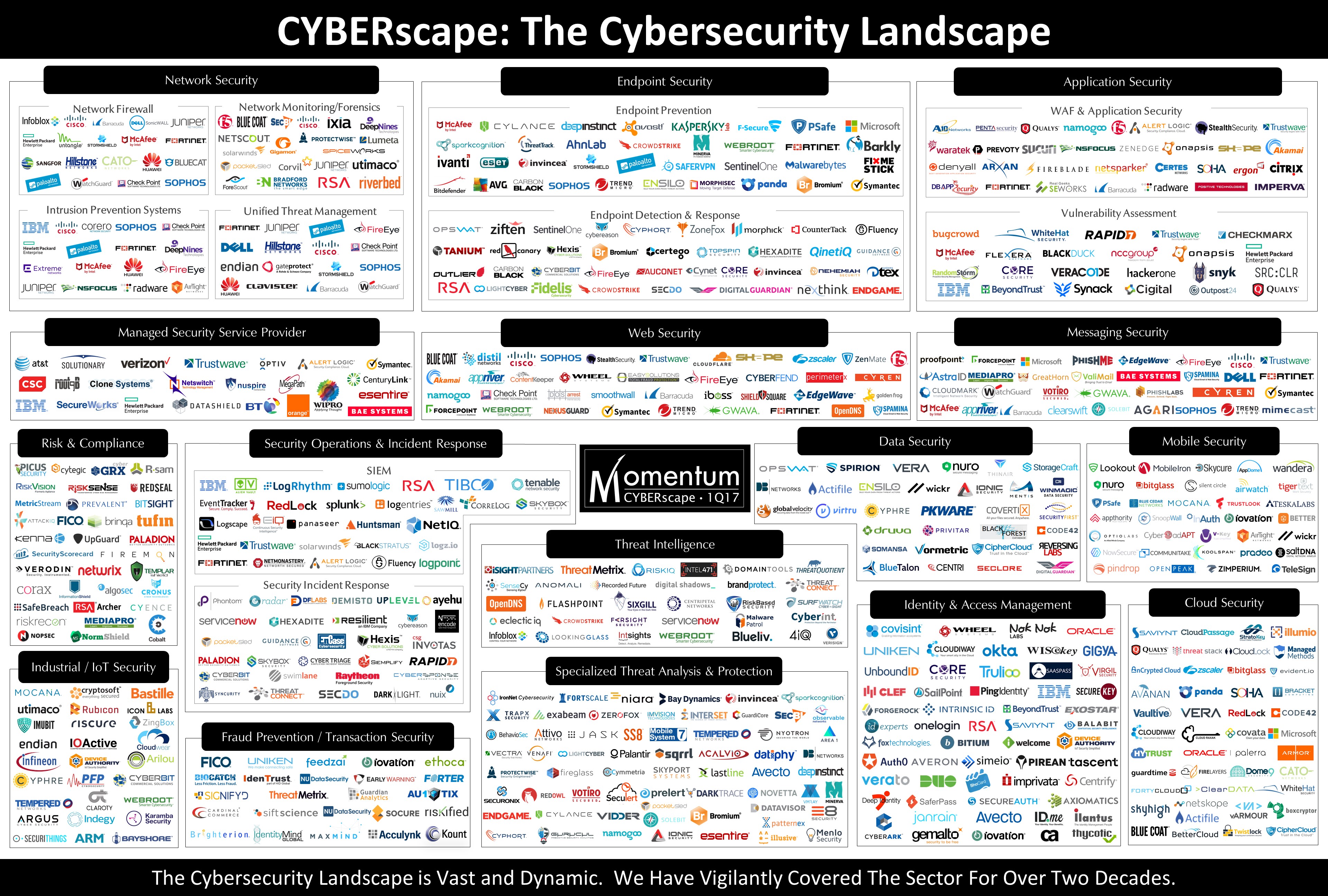
Source: Momentum Partners
Why mobile operators? In essence, the mobile operator is already performing the privacy protection measures to prevent rogue elements from stealing or controlling customer data, as well as network controls to prevent degradation of services, outages, and revenue loss. They already collect, manage and provide information about presence, availability and privacy policy of mobile users, and have many of the cybersecurity capabilities for their own internal use: infrastructure security, endpoint security including IoT security, application security, web/mobile security, monitoring capabilities, identity/access management, as well the ability to manage this as a service.
As newer business models emerge that will require engagement with multiple partners, and with product and service offerings being deployed in a distributed manner across enterprise-hosted servers to carrier-hosted data centers to partner-managed data centers, newer decentralized approaches to privacy management and security are needed. Take the example of an application such as the Connected Car and its associated functions:
- Autonomous driving
- Ride-sharing functions and interfaces
- Navigation and geo-location
- Infotainment and multimedia
- Location/context-based services, ads/promotions and commerce
- Telematics and diagnostics
- Condition monitoring and maintenance analytics
- In-vehicle concierge services
- etc.
Many of these Connected Car functions will be aggregated, integrated and provided by the car manufacturer in their vehicles with the mobile operator playing a critical partner role as an Auto-Mobile Operator. Additionally, with mobility comes roaming, with inter-carrier relationships. Also, resale of the vehicle will require portability of the Connected Car across consumers, carriers, and networks as well as application providers.
But the mobile operator will not be the only partner. There will be different parties that will engage in the Connected Car ecosystem that will need to transact and likely exchange personal data with each other to support the functions that enable the Connected Car. They will also require security to ensure the encryption and integrity of data across the participating community of Connect Car ecosystem players are maintained and policy controls are in place to ensure that authenticated and authorized applications and users in the ecosystem are using personal data properly. For example, should the in-vehicle concierge provider be able to track a user’s location at any time and see the history of locations travelled or only during a support session with the customer, and only the customer’s current location and diagnostic needs at the time of the call?
The Solution: Contextually-Aware Mobile Security as a Service
As computing becomes more ubiquitous and the volume of data that is implicitly and explicitly captured about us increases, the need for Contextually-Aware Mobile Security will become critical to personal data protection and policy enforcement as we traverse across a wider range of connected computing domains in our daily lives.
It happens that mobile operators are well positioned to develop and offer a range of cybersecurity and personal data management services that provide businesses with the integrated capabilities and functions that they need to comply with GDPR requirements while also providing consumers with the controls and transparency they need to manage their personal data with the businesses that they interact with on a daily basis in a secure computing/network environment.
The key to a holistic, Contextually-Aware Mobile Security framework is a Federated Identity Management (FIDM) capability that is able to manage the access and use (authorization) policies for an individual’s personal data in accordance to privacy regulations, such as GDPR. The FIDM platform would serve as a secure registry of an individual’s digital/network identity and broker access control between trusted parties in support of transactions and consented use of personal data that comply with the conditions of “lawful basis of processing” under GDPR or other personal data governance policies. Delivered as a managed service, FIDM functions can simplify the effort and investment of businesses to comply with GDPR regulations and processes.
Figure 4: Federated Identity Management (FIDM)
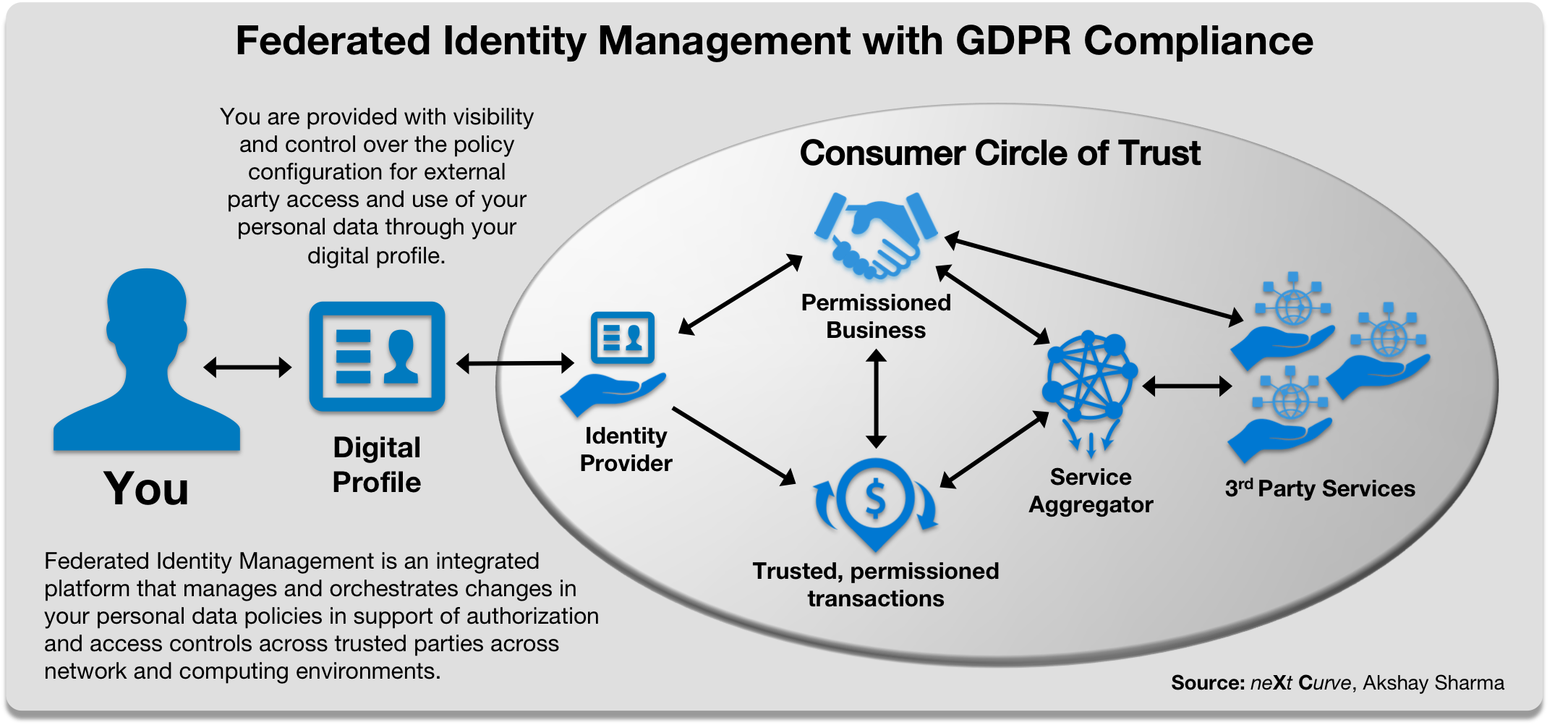
The FIDM function can be further extended by integrating it with existing databases like the HSS (home subscription server), and PCRF (policy charging and rules function) enforcement engines, as well as newer Blockchain-based registries and policy servers to ensure GDPR-compliance and controls are propagated across the mobile network and brokered to trusted 3rd parties. For the mobile operator, the FIDM platform can integrate and orchestrate the authentication and authorization of consumer and enterprise customers to their portfolio of virtual network services and converged IT/CT applications.
The FIDM will also enable mobile applications such as the Connected Car where an individual’s identity and personal data may need to be shared with multiple mobile operators and multiple 3rd parties that provide services that support Connect Car functions, some of which are mission critical. The FIDM will also be able to leverage the contextual information (user’s location, availability, preferences, etc.) that a mobile operator has to broker and orchestrate the authentication and authorization of access and sharing of personal data, including anonymizing/encrypting personal data at rest and in transit across network boundaries and transactional scenarios. Future retail applications will rely heavily on an FIDM capabilities as consumers are increasingly mobile and will engage in mixed-reality and digitally-augmented retail experiences such as the Apple Store and Amazon Go.
Figure 5: Mobile Security as a Service Platform with Blockchain
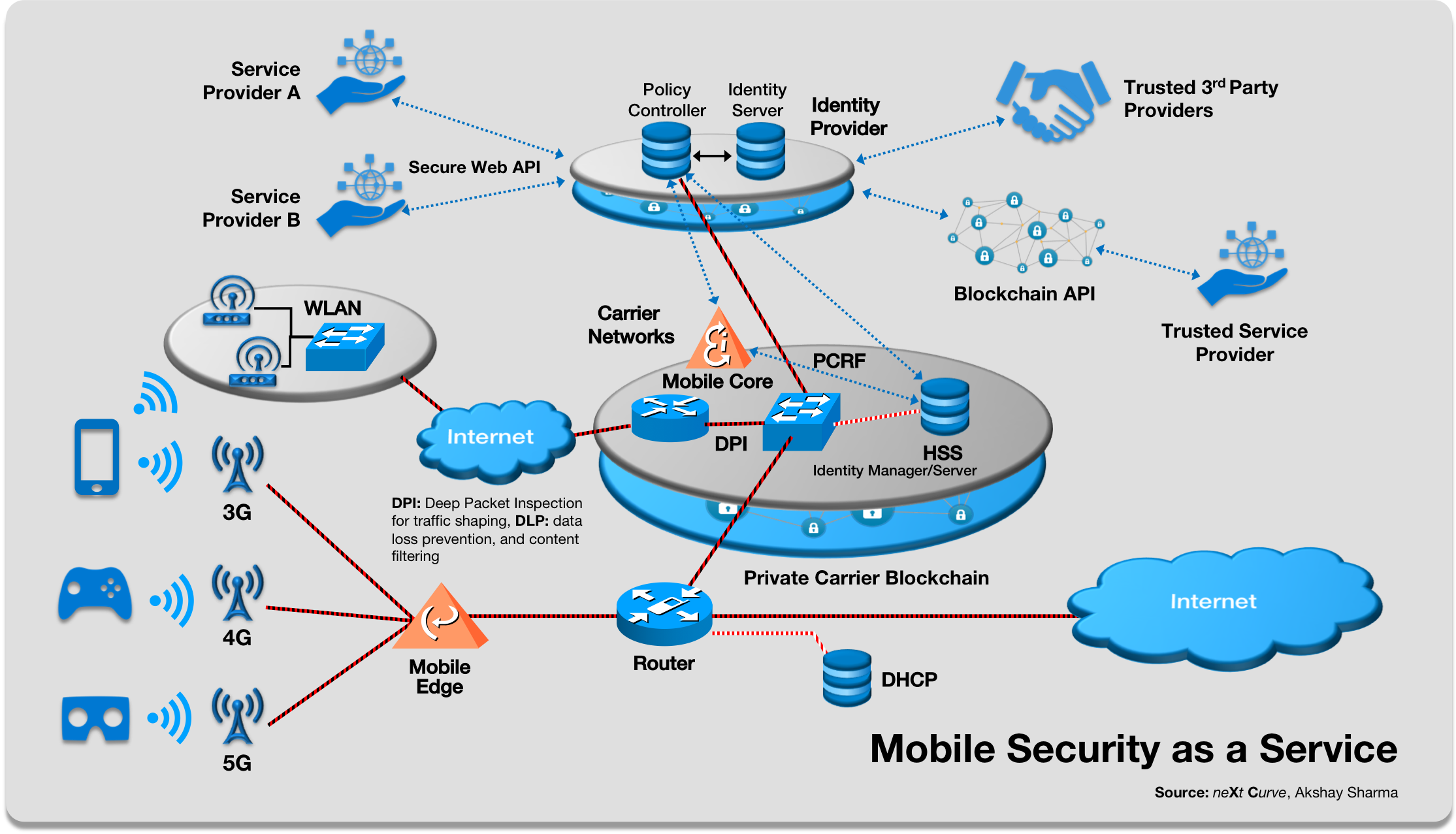
However, identity management and policy controls are not enough. Given that consumers spend much of their time on mobile networks and emerging 5G promises new cyberphysical applications that will rely heavily on personal data shared persistently and reliably between parties and 3rd party service providers, personal data will need to be secure and encrypted at rest and in transit across what will likely be an expanding, diverse universe of computing/network environments. To make matters more complicated, the Internet of Things presents a massive attack surface for your business and digital person with its numerous vulnerabilities to endpoint devices, network and applications, and now the processor due to Meltdown and Spectre and emerging derivatives.
Mobile operators can leverage mobile network security capabilities such as DPI (Deep Packet Inspection) and DLP (Data Loss Prevention) to monitor the conveyance of personal data within the network and increasingly into data centers that host carrier cloud services that will eventually be distributed to nano-datacenter as edge computing continues to evolve via IT/CT convergence and 5G/SDN/NFV transformation. While Meltdown and Spectre solutions are still works in progress, the mobile operator can be “proactive” and flag anomalies on the network like the 3AM botnet and track down messages sent to known suspicious sites and hostile states.
Besides active protection of the network, these network security functions can also provide enhanced monitoring of content and enable operators to apply granular policy controls on the use and availability of personal data to 3rd parties and businesses that individuals provide consent. These functions can also enable content filtering that gives the consumer fine-grained security controls on what they and their family want and don’t want to see and interact with.
Another area that the Contextually-Aware Mobile Security platform can address is IoT security. The securing of endpoint devices in the IoT context is vitally important as we are seeing a proliferation of IoT devices that will either capture, process, store or transmit/share what can and will be deemed personal data. At the moment, IoT security is a tremendous gap. As we have seen over the last couple of years, consumer IoT devices can be hacked and private information can be obtained:
- Video from consumers at home/work from video surveillance hacks,
- Consumer’s location at home can be obtained from motion sensors in HVAC sensors like the Nest Hack,
- IoT breaches have been across the board from automobiles, smartphones, HVAC thermostats to utility grids,
- There is also a significant problem associated with the reselling of personal IoT devices, which can be compromised and expose personal data.
Mobile operators can use Wireless LNP (local number portability) and applying it to IoT devices by leveraging SoftSIM or eSIM technologies to enhance the protection of personal data, as consumers and businesses alike “port” their IoT devices across different users, carriers, across networks (Wi-Fi, cellular, or newer spectrum in 5G, or legacy bands as in NB-IoT), and potentially across different cloud application providers like Amazon, Microsoft, Google. Combined with endpoint management, mobile operators can ensure that IoT devices have the latest security, software and firmware updates, which is particularly important in the age of Meltdown and Spectre.
Know Your Customer (KYC) is applicable within the blockchain world and in businesses in general. It is all about identifying your customer and verifying their personally identifiable information. Using the blockchain smart contracts with policies for consent management, as well as policies identifying who can view, update and transact with this data, a simple, accessible and immutable audit trail with policy controls exists with blockchain. Blockchain can also streamline the audit and compliance tasks for organizations while providing individuals with a platform to see who has interacted with their information, and with policy controls are able to opt-out to be “forgotten.”
Of course, all of these functions need to be administered and orchestrated under an integrated platform that is the Contextually-Aware Mobile Security as a Service platform. Through integrated, holistic control of network and compute services across the mobile network, the Contextually-Aware Mobile Security as a Service platform can orchestrate and automate many aspects of GDPR related compliance with remediation in the event of violation or security breach.
ReThinking Managed Security Services for IoT and GDPR
The Contextually-Aware Mobile Security solution model that we have described presents mobile operators with a platform to deliver a holistic suite of services that support the full lifecycle of security and personal data protection needed to help small and medium-sized businesses and large enterprises meet GDPR compliance requirements and quickly deploy compliant management processes for both their business and for their customer-facing applications. In effect, the service could significantly de-risk the current and ongoing operation of a company’s business in a GDPR/Privacy First world.
Figure 6: Mobile Carrier Security as a Service Offerings
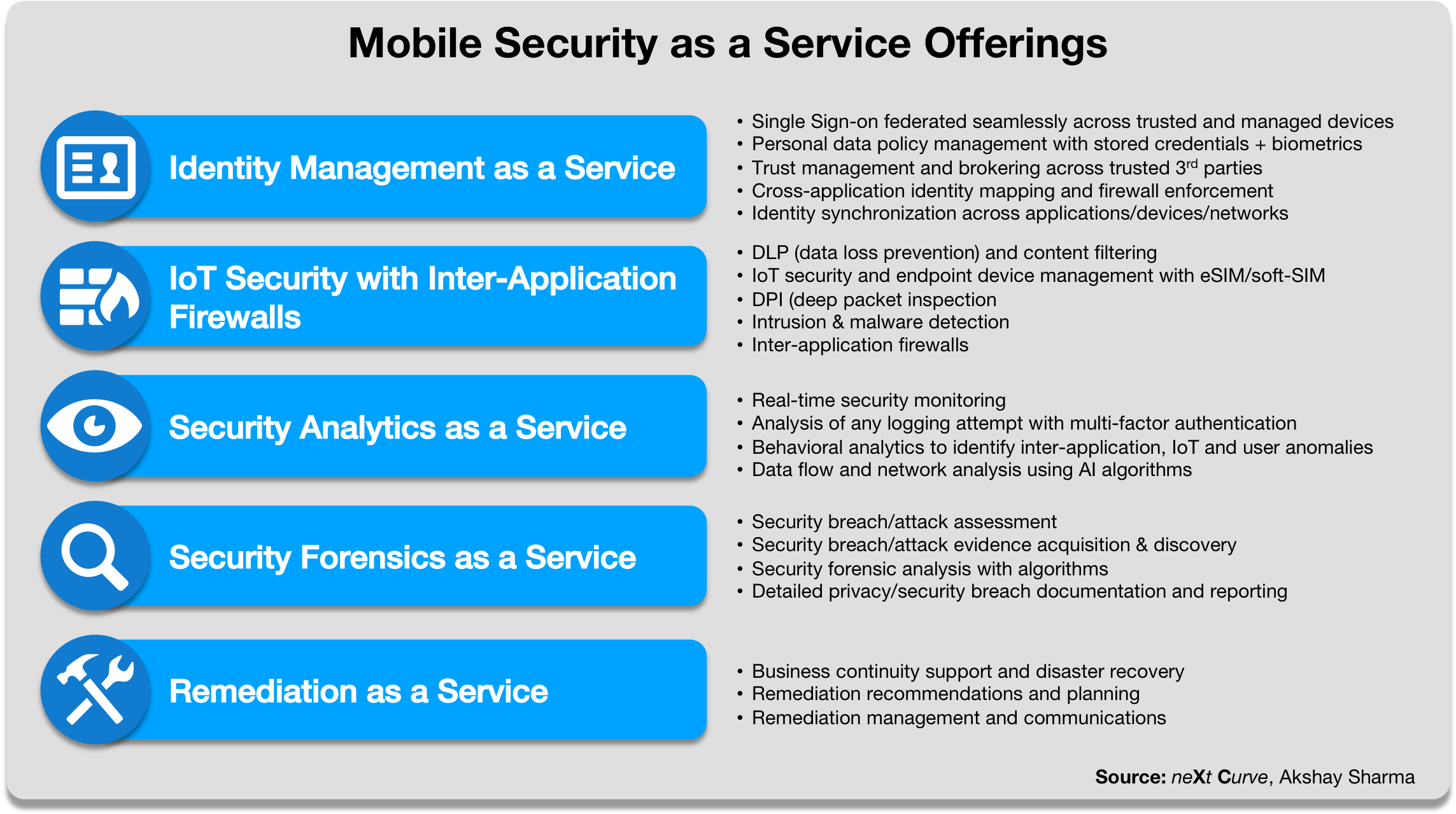
There are five components to the Mobile Security as a Service portfolio that can, if properly integrated, provide the full-lifecycle GDPR support and compliance/protection enablement as well as new service opportunities for mobile operators:
- Identity Management as a Service – Provides business customers with brokered authentication and authorization services and interfaces for accessing and managing the use of customer personal data within their enterprise as consented by their customers who are managed by the mobile operator. This service also provides consumers with an aggregated service to administer their consent policies across businesses that they engage with.
- IoT Security as a Service – Provides business customers with a secure network infrastructure to deploy new, customer-facing IoT applications to their customers with underlying management of personal data in compliance with GDPR or local privacy regulations. This service also provides businesses and consumers with holistic management and security administration of IoT endpoint devices and the personal data that is captured, stored and transmitted over the mobile network.
- Security Analytics as a Service – Provides business customers and consumers with continuous monitoring of the network, devices and applications to proactively detect anomalous behavior, cyberattacks and intrusions, and non-compliant use of personal data by leveraging advance analytics and algorithms to provide predictive insights into potential security incidents/events. This service can ensure that GDPR and other privacy policies are enforced by devices and parties on the network and the network itself.
- Security Forensics as a Service – Provides business customers with services that help them assess personal data compliance violations and cybersecurity breaches, discover and analyze forensic evidence that is a key input into remediation strategy and planning, business continuity, litigation and GDPR reporting and disclosure.
- Remediation as a Service – Provides business customers with advisory services and analysis to help customers design remediation strategies and plans to restore regulatory compliance, disaster recovery and business continuity, and to remedy any security vulnerabilities in the event of a security breach or violation of GDPR policy against a consumer or group of consumers. These services could also help customers propagate revocation of consent and manage confirmation of remediation action.
Developing and delivering this integrated portfolio of Contextually-Aware Security services will require mobile operators to think differently about their business and the implications (opportunities) of a Privacy First world. It will be important to design and implement a business model and business capabilities (BSS/OSS) that enable the mobile operator to monetize the value of their GDPR-compliant mobile security platform through an XaaS (Everything as a Service) model.
New Mobile Security as a Service Services Need New Capabilities
In order to deliver newer mobile security services, mobile operators will need to build new capabilities as well as the business models that will enable operators to monetize their investments in a Privacy First identity brokerage platform and the additional security infrastructure and functions needed to provide the secure network and computing environments that enable mission critical IoT applications such as the Connected Car and Digitally-Augmented Retail.
Figure 7: New Mobile Security as a Service Capabilities
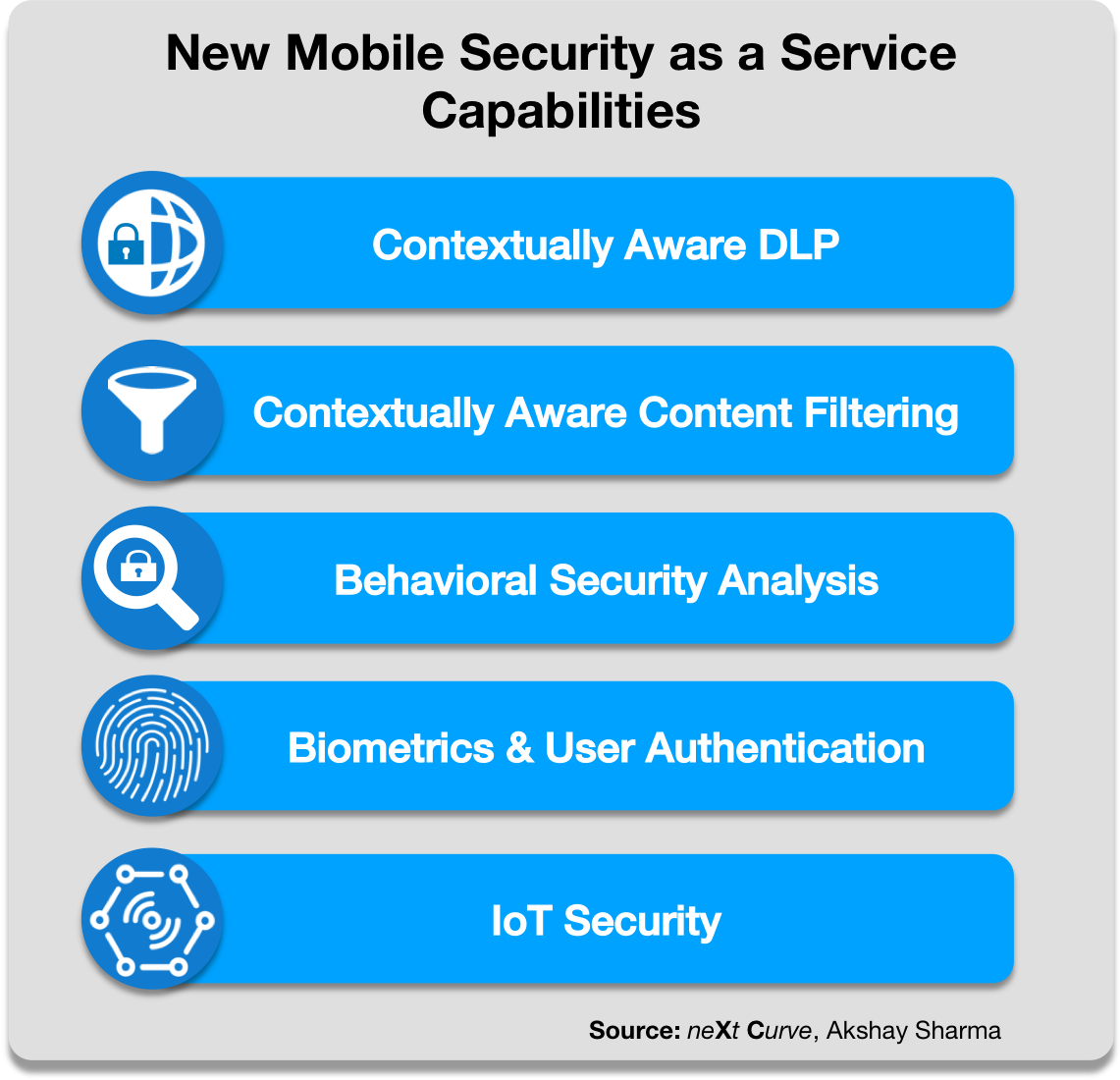
The following are key capability development areas that mobile operators need to focus on in order to realize a Contextually-Aware Mobile Security as a Service platform:
- Contextually-Aware DLP (Data Loss Protection) functions with GDPR-compliant policy controls and monitoring.
- Contextually-Aware Content Filtering functions with GDPR-compliant policy controls and monitoring enabled by DPI (Deep Packet Inspection).
- Behavioral Security Analytics enabled by AI/Machine Learning algorithms to enhance the detection of usage anomalies, attacks and intrusions.
- Enhanced Biometrics and User Authentication, with newer techniques like facial recognition, retinal scans, to newer Blockchain-based user identification approaches such as those considered in the UN’s ID 2020 initiatives.
- IoT Security with location tracking, firmware and software version control and endpoint device management using eSIM or SoftSIM authentication.
The development of these mobile security capabilities will likely involve the development and integration of in-house capabilities built around the mobile operators CT core, as well as with functions provided by trusted security and IT service provider partners especially as mobile operators continue their digital transformation journey driven by converged 5G, NFV, SDN and edge/cloud computing.
Implications for Business and Technology Leaders
Mobile operators are uniquely positioned to provide managed services that can integrate and broker the secure transaction and GDPR-compliant usage of personal data between consumers, businesses and other consented parties.
Mobile operators should build holistic security management platforms that apply advanced analytics and machine learning to intelligently monitor, analyze, optimize and remediate the security of computing environments and networks of their enterprise clients and consumers. The security services and capabilities that these platforms provide will be critical for securing IoT applications.
Mobile operators will need to work with a new ecosystem of partners to aggregate and develop their Contextually-Aware Mobile Security as a Service capabilities to meet the needs of 5G and converged IT/CT applications.
Business and technology leaders need to urgently recognize the need for a holistic approach to cybersecurity and understand the risks that cyber vulnerabilities and threats present to their business in a Privacy First future.
Business leaders also need to work closely with their technology leaders to understand the implications of GDPR on their current use of personal data and the potential impact GDPR requirements and restrictions will have on their business model going forward.
If you are interested in getting neXt Curve involved in helping you and your team ideate through new Contextually-Aware Mobile Security possibilities and opportunities, contact Leonard Lee at leonard.lee@next-curve.com. We can help your organization invent new service concepts and revenue streams that capitalize on the trend toward Privacy First consumer and business value.
You can also listen to the audio replay of our Contextually-Aware Mobile Security as a Service webcast by playing the media below or downloading the Podcast available on iTunes. Subscribe to our Podcast channel and keep up to date on the latest insights from neXt Curve.
Audio replay of the Contextually-Aware Mobile Security as a Service webcast
by Akshay Sharma
Research & Advisory Fellow, neXt Curve
and
Leonard Lee
Managing Director, neXt Curve
May 25, 2018
© 2018 neXt Curve. All rights reserved.
14 comments